Code Validation and Code Segregation
Provisioned Accounts
For each customer, BioT creates 2 cloud accounts:
- Development Account
- Production Account
Both accounts are applied with strict Identity and Access Management (IAM) permissions.
The following table describes the various environments which reside in each AWS Account.
| AWS Account | Description |
|---|---|
| Development | This is the working environment for the customer which provides isolation from the production environment. While developing plugins, its crucial to have a development environment where tests can be performed before going live. Some customers use this account for POC. |
| Production | Whereas a development environment may contain several different versions of a product or update being worked on and tested, a production environment contains just the final version of the product in order to avoid any confusion or security vulnerabilities. This account has additional security measurements, such as WAF and is configured to be Highly Available for making sure the system is resilient to any system failure. |
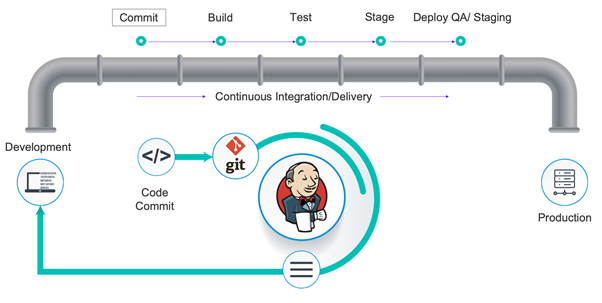
CI/CD Process Integrated Security & Code Scanning
BioT Leverage Continues Development and Continues Integration methodology making sure the code is bug free and has no viruses nor security vulnerabilities before released to customers.
Microservices Segregation
All services adhere to a permission control mechanism that governs their entitlements. For every service a role is defined and the associated permissions allowed for this role. JWT tokens are used to authenticate services and check for their run-time permissions.
Updated 6 months ago
